Should I delete a suspicious email?
What should you do with a suspicious email
Online MessagesDo not open it.Delete it immediately to prevent yourself from accidentally opening the message in the future.Do not download any attachments accompanying the message.Never click links that appear in the message.Do not reply to the sender.Report it.
CachedSimilar
Is deleting phishing email enough
One common mistake among most users and even IT administrators is they are deleting Spam and Malicious messages from their Inbox (those messages that bypass Anti-Spam). Deleting message just delete it and won't help anyone else. But you should mark it as Junk instead.
Cached
Does opening a suspicious email do anything
Just opening the phishing message without taking any further action will not compromise your data. However, hackers can still gather some data about you, even if all you did was open the email. They will use this data against you to create more targeted cyber attacks in the future.
Cached
What happens when you delete a spam email
Automatic deletion of emails
Once an email is deleted from the Trash or Spam folder, it cannot be recovered in the mailbox.
How do I delete suspicious emails
So, here are the five simple ways you can take to help eliminate spam emails.Mark as spam.Delete spam emails.Keep your email address private.Use a third-party spam filter.Change your email address.Unsubscribe from email lists.
What is a red flag in a suspicious email
Phishing emails often contain very generic greetings or even no greeting at all. Common generic greetings include “dear customer,” “dear account holder,” “dear user,” “dear sir/madam,” or “dear valued member.” If an email from an apparent trusted source does not address you directly by name, that could be a red flag.
Is it better to delete unwanted emails or unsubscribe
What to do: Ignore untrusted emails. While you should breathe easy about unsubscribing from legitimate emails, you are better off ignoring anything questionable that lands in your inbox. Henderson suggests deleting untrusted emails or blocking them for good by marking them as spam or junk.
What are 3 signs that an email is most likely a phishing email
An unfamiliar greeting. Grammar errors and misspelled words. Email addresses and domain names that don't match. Unusual content or request – these often involve a transfer of funds or requests for login credentials.
Can hackers do anything with just an email address
With just your email address, scammers can: Target you with sophisticated phishing emails. Find more sensitive information about you — including where you live. Attempt to hack into your other online accounts.
Can hackers get anything from your email
Access to your email can often be enough for hackers to commit all different types of identity theft. Remember, your email is like your online ID. Scammers can use it to sign you up for almost anything. Or, they can fake your online persona for other reasons.
Do spam emails go to junk
If your email contains a large amount of spam words, the server will block your email or send it to junk folders. There are certain words that will trigger spam filters, so it's best to use these sparingly or avoid using them completely.
Why am I suddenly getting so many spam emails
But, if you suddenly started receiving dozens of spam emails, chances are, your address has been exposed. Websites like Have I Been Pwned check if your personal data was compromised. These services work like search engines — just enter your email address and they will look through exposed data.
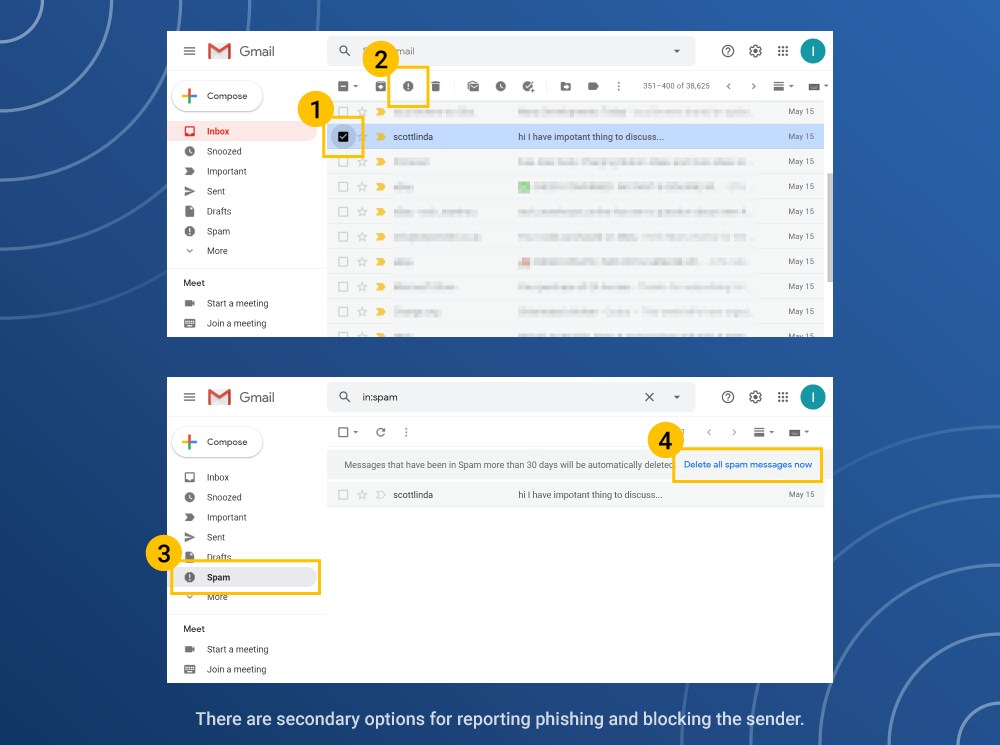
Can you block a suspicious email
Block an email address
When you block a sender, messages they send you will go to your Spam folder. On your Android phone or tablet, open the Gmail app . Open the message. Tap Block [sender].
What does a suspicious email look like
Grammar errors and misspelled words. Email addresses and domain names that don't match. Unusual content or request – these often involve a transfer of funds or requests for login credentials. Urgency – ACT NOW, IMMEDIATE ACTION REQUIRED.
What are 3 signs that a suspicious email may be a phishing email
Frequently Asked QuestionsAn unfamiliar greeting.Grammar errors and misspelled words.Email addresses and domain names that don't match.Unusual content or request – these often involve a transfer of funds or requests for login credentials.Urgency – ACT NOW, IMMEDIATE ACTION REQUIRED.
What happens if you reply to a suspicious email
First, replying to a phishing email provides the scammer with a copy of your company's email signature, which might include phone numbers and other information. This signature could enable them to craft more convincing spearphishing templates, as well as giving them more potential targets.
How do I stop spam emails permanently
This Article Contains:Report the email as spam.Block spam email addresses.Change your email privacy settings.Unsubscribe from unwanted newsletters or mailing lists.Use a secondary email address.Use a third-party email filter.Delete suspicious emails.Protect your device against malicious spam.
Why is deleting unwanted emails good
Over half of all email traffic is considered spam say figures from Statista. With 239.6 billion messages sent around the world, that's a lot of spam. Deleting these messages frees up space on the servers that store email data and could help reduce the amount of CO2 produced by systems keeping us all online.
What could be a red flag of a phishing email
Phishing emails often contain very generic greetings or even no greeting at all. Common generic greetings include “dear customer,” “dear account holder,” “dear user,” “dear sir/madam,” or “dear valued member.” If an email from an apparent trusted source does not address you directly by name, that could be a red flag.
What are 5 ways you spot a phishing email
How to Spot a Phishing EmailThe email is sent from a public domain email address. Look at the sender's email address.It contains a strange or unexpected attachment.It creates a sense of urgency.It links to an unfamiliar or misspelled email address.It contains spelling or grammatical errors.
