What are 3 signs of a phishing email?
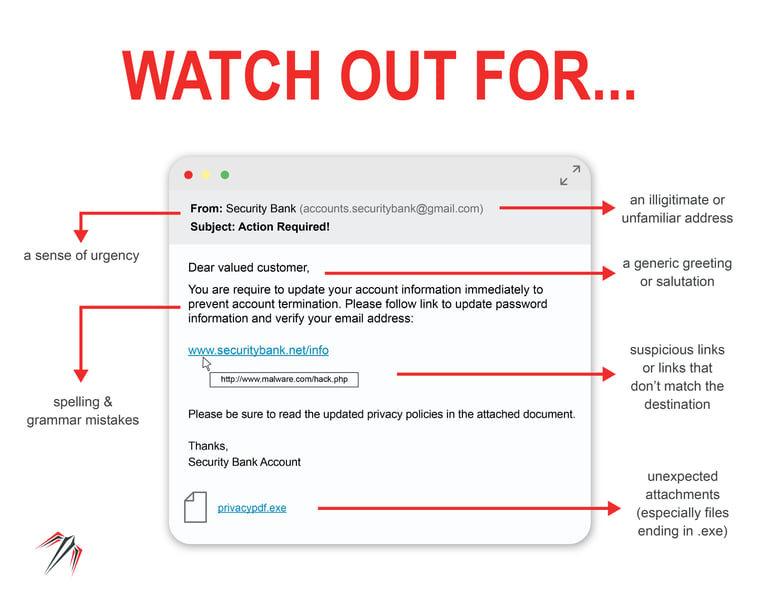
What are 4 common indications that an email is a phishing attempt
Some common indicators of a phishing attempt are:Generic or Strange Greetings.Unusually-worded Subject Lines.An Offer That Seems Too Good to Be True.Unknown, Unusual, or Public Domain.Blatant Grammatical or Spelling Errors.Suspicious Links or Attachments.Origin of Sender and Request Type.
Cached
How do I know if an email is phishing
Emails that contain the following should be approached with extreme caution, as these are common traits of phishing email:Urgent action demands.Poor grammar and spelling errors.An unfamiliar greeting or salutation.Requests for login credentials, payment information or sensitive data.Offers that are too good to be true.
What are 5 ways you spot a phishing email
How to Spot a Phishing EmailThe email is sent from a public domain email address. Look at the sender's email address.It contains a strange or unexpected attachment.It creates a sense of urgency.It links to an unfamiliar or misspelled email address.It contains spelling or grammatical errors.
What is the most common indicator of a phishing email
5 Common Indicators of a Phishing AttemptSpelling errors.Unusual requests.Strange email content.Personal information solicitation.Unfamiliar email addresses.
Cached
What are 4 clues to determine phishing
What is a common indicator of a phishing attack Requests for personal information, generic greetings or lack of greetings, misspellings, unofficial "from" email addresses, unfamiliar webpages, and misleading hyperlinks are the most common indicators of a phishing attack.
What happens if you open a phishing email
Just opening the phishing message without taking any further action will not compromise your data. However, hackers can still gather some data about you, even if all you did was open the email. They will use this data against you to create more targeted cyber attacks in the future.
How can you confirm if an email request is legitimate
7 Tips for How to Tell If an Email Is FakeInspect the Email Header Info to Verify Whether the Sender's Address is Legitimate.Watch Out For Uncommon Uses of the Email Bcc Field.Check Whether Embedded Links Redirect to Unexpected Websites.Pay Attention: Don't Ignore Unusual Spelling and Grammatical Errors.
What is a typical phishing email
The email might read something like, “We've updated our login credential policy. Please confirm your account by logging into Google Docs.” The sender's email is a faked Google email address, [email protected].
Which of the following is a phishing email red flag
Incorrect (but maybe similar) sender email addresses. Links that don't go to official websites. Spelling or grammar errors, beyond the odd typo, that a legitimate organization wouldn't miss.
What are the 7 red flags of phishing
The 7 Red Flags of PhishingUrgent or Threatening Language. Real emergencies don't happen over email.Requests for Sensitive Information.Anything Too Good to be True.Unexpected Emails.Information Mismatches.Suspicious Attachments.Unprofessional Design.
What are two of the most common phishing attacks
Below are some of the most common phishing techniques attackers will employ to try to steal information or gain access to your devices.Invoice phishing.Payment/delivery scam.Tax-themed phishing scams.Downloads.Phishing emails that deliver other threats.Spear phishing.Whaling.Business email compromise.
Can someone steal your information if you open an email
Just opening the phishing message without taking any further action will not compromise your data. However, hackers can still gather some data about you, even if all you did was open the email. They will use this data against you to create more targeted cyber attacks in the future.
Do I delete phishing emails
If you receive a spam email, you should delete it immediately—do not open any attachments or click any links. It only takes one wrong click, and hackers can gain access to your entire computer. The tips below will help you better protect yourself when using email. Phishing emails are one type of email scam.
How should I verify my email
Sign in to your email to verify your account
While you're creating your account, you'll get an email from Google. Open the email and find the verification code.
Is there a way to verify an email
How do you verify an email addressUse an Email Verification tool. An Email Verification tool is the fastest, easiest, and most effective way to verify emails at scale.Ping the Server.Google search the address.
What is a famous example of phishing
The Nordea Bank Incident
Dubbed the "biggest ever online bank heist" by digital security company McAfee, Nordea customers were hit with phishing emails containing Trojan viruses that installed a keylogger into the victims' computers and directed them to a fake bank website where hackers intercepted login credentials.
What are examples of phishing emails
The email might read something like, “We've updated our login credential policy. Please confirm your account by logging into Google Docs.” The sender's email is a faked Google email address, [email protected].
Which of these is an example of a phishing email
For example: The user is redirected to myuniversity.edurenewal.com, a bogus page appearing exactly like the real renewal page, where both new and existing passwords are requested. The attacker, monitoring the page, hijacks the original password to gain access to secured areas on the university network.
What are the 2 most common types of phishing attacks
The 5 Most Common Types of Phishing AttackEmail phishing. Most phishing attacks are sent by email.Spear phishing. There are two other, more sophisticated, types of phishing involving email.Whaling. Whaling attacks are even more targeted, taking aim at senior executives.Smishing and vishing.Angler phishing.
What is the number one target for phishing attacks
Often phishers are targeting an enterprise and a selected group at an office (staff, management, executives) that is responsible for a project or service.
