What are signs of a data breach?
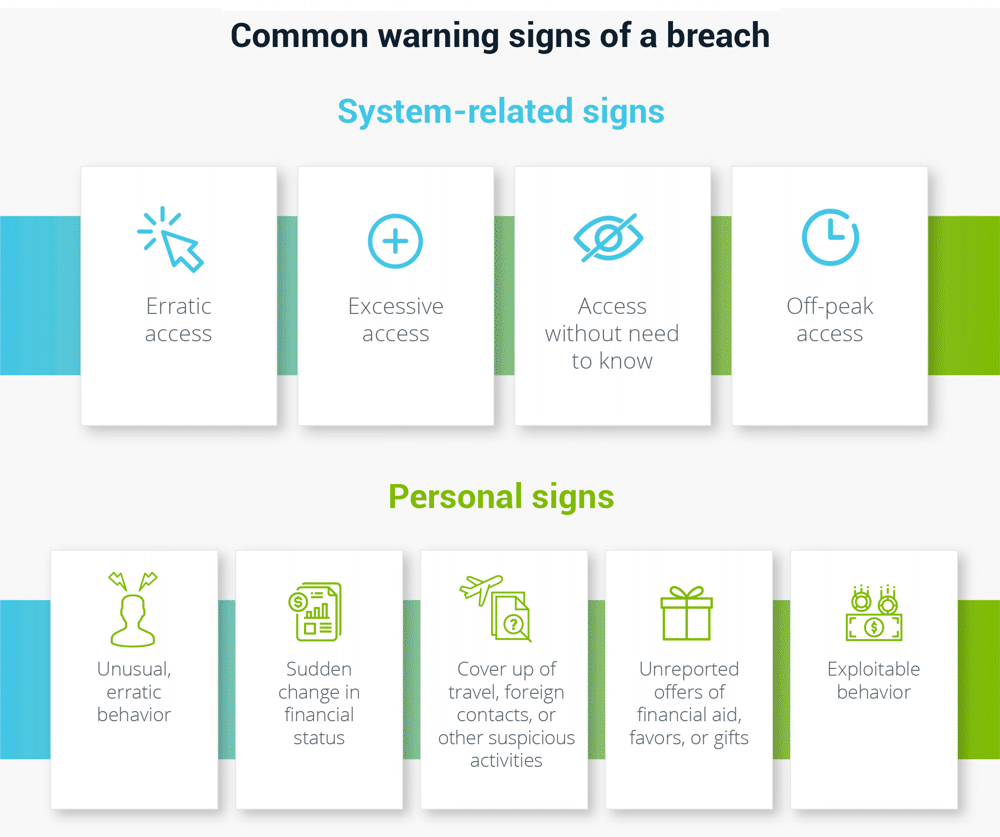
How do you know if your personal data has been leaked
Visit Have I Been Pwned
The search engine allows you to search either by your email address or phone number and will flag any breaches containing your data when they happen by cross-checking billions of leaked records added to the Have I Been Pwned database.
Cached
What are the 3 elements of data breach
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability.
What are the 4 common causes of data breaches
Six Common Causes of Data BreachesCause 1. Insider Threats Due to Misuse of Privileged Access.Cause 2. Weak and Stolen Passwords.Cause 3. Unpatched Applications.Cause 4. Malware.Cause 5. Social Engineering.Cause 6. Physical Attacks.
What are examples of data breaches
Let's take a glance at the most common types of data breaches and how they affect the business.Hacking Intrusions.Insider Threat.Data on the Move.Physical Theft.Human Error.Accidental Internet Exposure.Unauthorized Access.
Does a data leak mean I’ve been hacked
If a company with your information has a data breach, there are a few important steps you can take to stay ahead of hackers and protect yourself from identity theft. Remember, a breach doesn't automatically mean your identity has been stolen.
What can I do if my personal data has been breached
72 hours – how to respond to a personal data breachStep one: Don't panic.Step two: Start the timer.Step three: Find out what's happened.Step four: Try to contain the breach.Step five: Assess the risk.Step six: If necessary, act to protect those affected.Step seven: Submit your report (if needed)
What are the 4 types of breach
Generally speaking, there are four types of contract breaches: anticipatory, actual, minor and material.Anticipatory breach vs. actual breach.Minor breach vs. material breach.What's next: Types of remedies for broken contracts.
What is the most common method of data breach
Hacking attacks may well be the most common cause of a data breach but it is often a weak or lost password that is the vulnerability that is being exploited by the opportunist hacker.
What is the most common source of a data breach
Criminal hacking—it's what causes the majority of data breaches. These are planned attacks by cybercriminals always looking to exploit computer systems or networks. Some common techniques include phishing, password attacks, SQL injections, malware infection, and DNS spoofing.
What are the three biggest data breaches of all time
Top 23 Biggest Data Breaches in US History1. Yahoo! Date: 2013-2016.Microsoft. Date: January 2023.First American Financial Corp. Date: May 2023.4. Facebook. Date: April 2023.LinkedIn. Date: April 2023.JPMorgan Chase. Date: June 2014.Home Depot. Date: April 2014.MySpace. Date: June 2013.
What is the most common data breach
The 7 Most Common Types of Data Breaches and How They Affect Your BusinessStolen Information.Password Guessing.Recording Keystrokes.Phishing.Malware or Virus.Distributed Denial of Service (DDoS)
What is the most popular data breach
Top 23 Biggest Data Breaches in US History1. Yahoo! Date: 2013-2016.Microsoft. Date: January 2023.First American Financial Corp. Date: May 2023.4. Facebook. Date: April 2023.LinkedIn. Date: April 2023.JPMorgan Chase. Date: June 2014.Home Depot. Date: April 2014.MySpace. Date: June 2013.
What are the 2 possible signs that you have been hacked
Common warning signs of a cyberhackPassword reset emails.Random popups.Contacts receiving fake emails or text messages from you.Redirected internet searches.Computer, network, or internet connection slows down.Ransomware messages.
Should I be worried if my password is in a data leak
The notice informs you that your login credentials have been compromised during a cyberattack or your password is leaked in a data breach. The usual recommendation is that you should immediately change your account password.
How serious is a data breach
A data breach can easily result in identity theft when sensitive information is exposed to unauthorised individuals. Hackers can use this information to steal a person's identity and commit fraudulent activities, such as opening new accounts or making unauthorised purchases.
How quickly should a data breach be reported
within 72 hours
What is data breach reporting Under the GDPR, new obligations have been imposed for all businesses to report certain types of personal data breaches to the ICO within 72 hours of the business becoming aware of the breach.
What are the most common breaches
The 7 Most Common Types of Data Breaches and How They Affect Your BusinessStolen Information.Password Guessing.Recording Keystrokes.Phishing.Malware or Virus.Distributed Denial of Service (DDoS)
What is the most common type of record compromised in a breach
Guessing and stealing passwords of millions of users is one of the most frequent types of data breaches.
What are three of the top five causes of breaches
The use of weak passwords; Sending sensitive information to the wrong recipients; Sharing password/account information; and. Falling for phishing scams.
What is the most common source for data breaches
Criminal hacking—it's what causes the majority of data breaches. These are planned attacks by cybercriminals always looking to exploit computer systems or networks. Some common techniques include phishing, password attacks, SQL injections, malware infection, and DNS spoofing.
