What are the 4 C’s security?
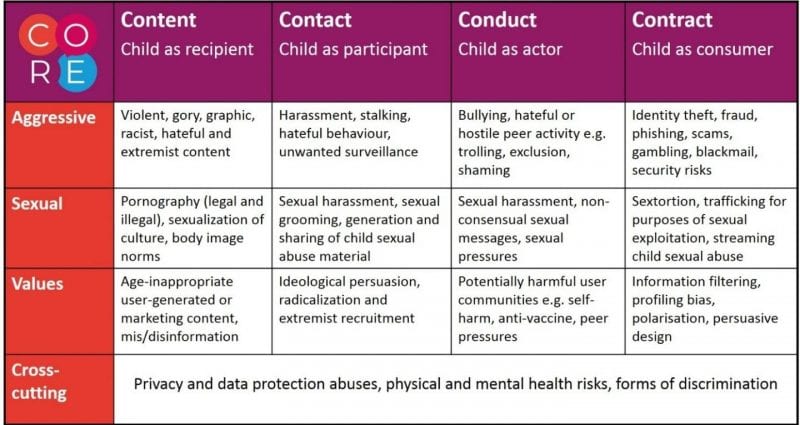
What are 4C in security
The 4C's of Cloud Native security are Cloud, Clusters, Containers, and Code. Note: This layered approach augments the defense in depth computing approach to security, which is widely regarded as a best practice for securing software systems.
What are the four C’s mod
The 4Cs for marketing communications: Clarity; Credibility; Consistency and Competitiveness.
What is container security
Container security is the process of implementing security tools and policies to assure that all in your container is running as intended, including protection of infrastructure, software supply chain, runtime, and everything between. Related Names. Secure Host.
What is Kubernetes security
Kubernetes security is an open-source system for automating the deployment, scaling, and management of containerized applications. It is easier to manage, secure, and discover containers when they are grouped into logical units, and Kubernetes is the leading container management system in the market today.
What are the 4 C’s of success
Are you familiar with the Four Cs I first discovered them in Yaval Noah Harari's “21 Lessons for the 21st Century.” They are: critical thinking, creativity, collaboration and communication.
What are the 4 forms of security
There are four main types of security: debt securities, equity securities, derivative securities, and hybrid securities, which are a combination of debt and equity.
What are the 4 C’s content
This is where the four C's of marketing come in – consumer, cost, convenience, and communication. Unlike the 4Ps, which offer a seller-oriented approach, the 4Cs provide a more consumer-based perspective on the marketing strategy.
What are the 4 C’s in
The 4 Cs of Food SafetyCleaning.Cooking.Cross contamination.Chilling.Contact.
What is an example of container security
Popular examples include Amazon Elastic Kubernetes Service (Amazon EKS), Google Kubernetes Engine (GKE), Azure Kubernetes Service (AKS), Docker, OpenShift, and Nomad.
How do you ensure container security
Container Security Best Practices and Suggested SolutionsUse trusted base images.Keep images up to date.Reduce the attack surface.Limit container privileges.Implement access controls.Scan images for vulnerabilities.Implement network security.Monitor container activity.
What are the security principles of Kubernetes
Kubernetes security is built on the model of securing in layers – specifically: cloud infrastructure, clusters, containers, and code. The underlying approach to Kubernetes security is one of defense in depth. This is a perfect complement to the layered approach that can ultimately provide redundancy against exploits.
What are the security components of Kubernetes
It consists of components such as kubelet, kube-proxy and container runtime. The container runtime is the software that is responsible for running containers. This cheatsheet provides a starting point for securing Kubernetes cluster.
What are the 4 C’s of leadership
The importance of the four C's in leadership: Candor, Commitment, Courage and Competence are necessary to maintain strong and effective soldiers. A reflection of a good leader shows in his followers.
What are the 4 C’s of common core
The 21st-century skills of communication, collaboration, creativity, and critical thinking, often referred to as the “four Cs,” are an integral part of the Common Core standards.
What are the 4 types of responsibilities of private security
physical security, 2. personnel security, 3. information systems security, 4. investigations, 5.
What are the 4Cs and why are they important
In the health and social care sector, the four C's are especially important for food hygiene safety. Cleaning, Cooking, Cross-contamination and Chilling all come into play during the food handling process and must be implemented properly at all times.
What are the 4Cs of success
Are you familiar with the Four Cs I first discovered them in Yaval Noah Harari's “21 Lessons for the 21st Century.” They are: critical thinking, creativity, collaboration and communication.
What does SOC mean in containers
shipper-owned container
A shipper-owned container (SOC) is a freight shipping container owned by an independent individual or business.
What are three security examples
These include management security, operational security, and physical security controls.
What are the three main ways in which security can be provided
These include management security, operational security, and physical security controls.
