What do suspicious emails look like?
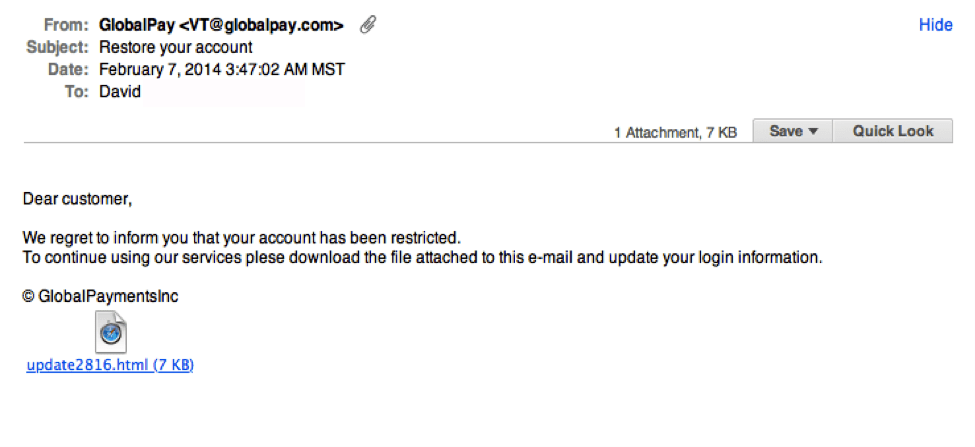
How does a spam email look like
While many spam emails trick victims with complex, made-up threats and rewards, others use short one-liners. They often contain nothing but links. The anchor text will likely use weird, open-ended statements to pique your curiosity and encourage you to visit their page. Avoid interacting with these messages.
Cached
How do you check if an email is legit
How to Check if an Email Address is ValidMethod 1: Send an Email to the Address. Perhaps the most straightforward way how to check if an email is valid is to send a message to it.Method 2: Password Recovery.Method 3: Perform an IP Address Lookup.Method 4: Search the Address in Google.Method 5: Email Checker.
Does opening a suspicious email do anything
Just opening the phishing message without taking any further action will not compromise your data. However, hackers can still gather some data about you, even if all you did was open the email. They will use this data against you to create more targeted cyber attacks in the future.
Cached
What are four warning signs that an email is a phishing
How To Recognize Phishingsay they've noticed some suspicious activity or log-in attempts — they haven't.claim there's a problem with your account or your payment information — there isn't.say you need to confirm some personal or financial information — you don't.include an invoice you don't recognize — it's fake.
Cached
What are two main signs of spam emails
Major warning signs in an email are:An unfamiliar greeting.Grammar errors and misspelled words.Email addresses and domain names that don't match.Unusual content or request – these often involve a transfer of funds or requests for login credentials.Urgency – ACT NOW, IMMEDIATE ACTION REQUIRED.
What are three warning signs that an email contain malware
a)It contains a strange attachment. b)It's from someone I don't know. c)The link doesn't look like it goes to an official page.
What happens if a scammer has your email address
If a hacker has your email address, he has half of your confidential information – all that's remaining is your password. And they can gain that by sending you a phishing email saying that your account has been accessed from a new device or compromised.
How do I identify an email
How to find someone's email address [Summary]:Google Name + “Email”Google Name + Place of Work.Search LinkedIn.Search their company website.Use Google's site search operator.Use advanced Google search operators.Try some “kitchen sink” queries.Check social media profiles.
What if I clicked on a suspicious email
Upon clicking the link, malware can be downloaded onto the user's device to spy on their activity or collect their data. The malware will appear to run as a legitimate download. It can then hide in legitimate folders and not do anything malicious instantly, leaving the victim thinking they just opened a remittance pdf.
Is it safe to delete suspicious email
If you receive a spam email, you should delete it immediately—do not open any attachments or click any links. It only takes one wrong click, and hackers can gain access to your entire computer. The tips below will help you better protect yourself when using email. Phishing emails are one type of email scam.
What are the 7 red flags of phishing
The 7 Red Flags of PhishingUrgent or Threatening Language. Real emergencies don't happen over email.Requests for Sensitive Information.Anything Too Good to be True.Unexpected Emails.Information Mismatches.Suspicious Attachments.Unprofessional Design.
What are 2 things you should look for to determine if an email is phishing
Emails that contain the following should be approached with extreme caution, as these are common traits of phishing email:Urgent action demands.Poor grammar and spelling errors.An unfamiliar greeting or salutation.Requests for login credentials, payment information or sensitive data.Offers that are too good to be true.
What are red flags in email
Information Mismatches
Incorrect (but maybe similar) sender email addresses. Links that don't go to official websites. Spelling or grammar errors, beyond the odd typo, that a legitimate organization wouldn't miss.
What is a common indicator of a phishing
Generic signatures and a lack of contact information are also strong indicators of phishing emails. Legitimate organizations generally provide their contact information. If there is no phone number, email address, or social media links in the signature block, the email is almost always fake.
What is an indicator of malicious email
Spelling errors
Of course, everyone makes a spelling or grammar mistake from time to time, but phishing attempts are often riddled with them. If an email contains multiple indicators on this list and numerous spelling and grammatical errors, it's probably a scam.
How can you tell if an email is malicious
How to Spot a Phishing Email: With ExamplesThe message is sent from a public email domain.The domain name is misspelt.The email is poorly written.It includes suspicious attachments or links.The message creates a sense of urgency.Prevent phishing by educating your employees.
Can someone hack my bank account with my email address
It's also possible hackers could use your email account to gain access to your bank account or credit card information, draining funds from an account, or racking up charges. They might even use your email and password to sign up for online sites and services, sticking you with monthly fees in the process.
Can someone hack your email with just your email address
With just your email address, scammers can: Target you with sophisticated phishing emails. Find more sensitive information about you — including where you live. Attempt to hack into your other online accounts.
What are three warning signs that an email contains malware
a)It contains a strange attachment. b)It's from someone I don't know. c)The link doesn't look like it goes to an official page.
What is the difference between a phishing email and a legitimate email
Most legitimate requests will not direct users to a website that is different from the sender's domain. By contrast, phishing attempts often redirect users to a malicious site or mask malicious links in the email body. The CTA includes a link to the sender's website.
