What does a suspicious email look like?
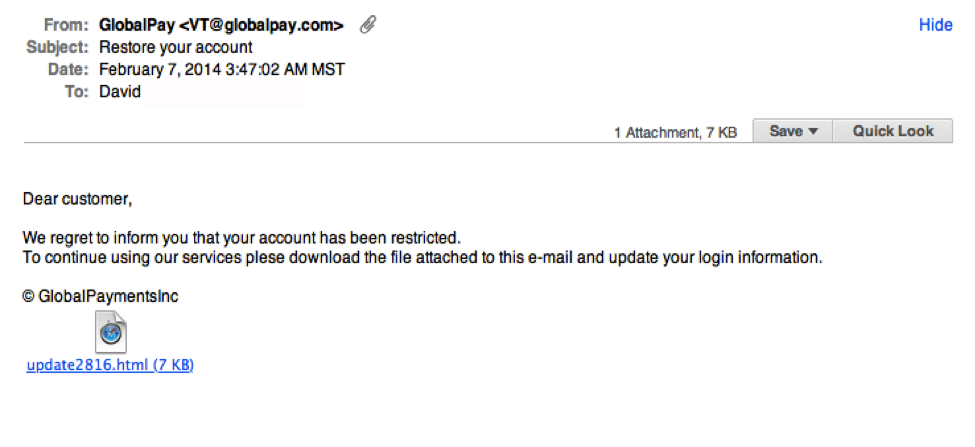
Which of the following are signs of a suspicious email
Frequently Asked QuestionsAn unfamiliar greeting.Grammar errors and misspelled words.Email addresses and domain names that don't match.Unusual content or request – these often involve a transfer of funds or requests for login credentials.Urgency – ACT NOW, IMMEDIATE ACTION REQUIRED.
Cached
What makes an email look suspicious
Poor grammar and spelling errors. An unfamiliar greeting or salutation. Requests for login credentials, payment information or sensitive data. Offers that are too good to be true.
How do I check if an email address is legitimate
Here are five ways to detect a fake email address:Check the Email Address Domain. A common way to spot a fake email address is to check its hosted domain.Examine the Sender's Display Name.Look for Misspelt Words.Hover Over Any Links and Attachments.Verify the Sender's Information by Contacting Them Directly.
How does a spam email look like
While many spam emails trick victims with complex, made-up threats and rewards, others use short one-liners. They often contain nothing but links. The anchor text will likely use weird, open-ended statements to pique your curiosity and encourage you to visit their page. Avoid interacting with these messages.
Cached
What is a red flag in a suspicious email
Phishing emails often contain very generic greetings or even no greeting at all. Common generic greetings include “dear customer,” “dear account holder,” “dear user,” “dear sir/madam,” or “dear valued member.” If an email from an apparent trusted source does not address you directly by name, that could be a red flag.
Which of the following is a red flag in a suspicious email
Incorrect (but maybe similar) sender email addresses. Links that don't go to official websites. Spelling or grammar errors, beyond the odd typo, that a legitimate organization wouldn't miss.
What are four warning signs that an email is a phishing
How To Recognize Phishingsay they've noticed some suspicious activity or log-in attempts — they haven't.claim there's a problem with your account or your payment information — there isn't.say you need to confirm some personal or financial information — you don't.include an invoice you don't recognize — it's fake.
What happens if a scammer has your email address
If a hacker has your email address, he has half of your confidential information – all that's remaining is your password. And they can gain that by sending you a phishing email saying that your account has been accessed from a new device or compromised.
How can I verify an email account
As i mentioned previously. There are two main ways to verify your email address with bonjour via oauth or domain verification. The first of the two methods oauth is a good fit if you're looking to
What are three warning signs that an email contain malware
a)It contains a strange attachment. b)It's from someone I don't know. c)The link doesn't look like it goes to an official page.
When should you be suspicious of an email
The email is poorly written
You can often tell if an email is a scam if it contains poor spelling and grammar. Many people will tell you that such errors are part of a 'filtering system' in which cyber criminals target only the most gullible people.
What are the 7 red flags of phishing
The 7 Red Flags of PhishingUrgent or Threatening Language. Real emergencies don't happen over email.Requests for Sensitive Information.Anything Too Good to be True.Unexpected Emails.Information Mismatches.Suspicious Attachments.Unprofessional Design.
What is a common indicator of phishing
Generic signatures and a lack of contact information are also strong indicators of phishing emails. Legitimate organizations generally provide their contact information. If there is no phone number, email address, or social media links in the signature block, the email is almost always fake.
Can someone hack my bank account with my email address
It's also possible hackers could use your email account to gain access to your bank account or credit card information, draining funds from an account, or racking up charges. They might even use your email and password to sign up for online sites and services, sticking you with monthly fees in the process.
Can someone hack your email with just your email address
With just your email address, scammers can: Target you with sophisticated phishing emails. Find more sensitive information about you — including where you live. Attempt to hack into your other online accounts.
What happens when you verify your email
What is Email Verification Email verification is the process of making sure the emails on your list are tied to an inbox. In other words, it's making sure that the messages you're sending have somewhere to go. List Verification is the process of removing undeliverable or dangerous emails from your list.
Is there a way to verify a Gmail account
Follow the steps to confirm it's your account.If you entered a phone number, enter the code sent to that phone.If you entered a recovery email address, check its inbox for an email from Google. Enter the code from the email.
Can I get a virus from opening an email
Can I get a virus by reading my email messages Most viruses, Trojan horses, and worms are activated when you open an attachment or click a link contained in an email message. If your email client allows scripting, then it is possible to get a virus by simply opening a message.
Which is the common red flags of phishing emails
Phishing emails often contain very generic greetings or even no greeting at all. Common generic greetings include “dear customer,” “dear account holder,” “dear user,” “dear sir/madam,” or “dear valued member.” If an email from an apparent trusted source does not address you directly by name, that could be a red flag.
What are 4 clues to determine phishing
What is a common indicator of a phishing attack Requests for personal information, generic greetings or lack of greetings, misspellings, unofficial "from" email addresses, unfamiliar webpages, and misleading hyperlinks are the most common indicators of a phishing attack.
